Ad fraud has been a recurring topic and threat to programmatic advertising and is showing little sign of slowing down.
Industry research by cybersecurity company CHEQ revealed that fraudulent activities committed against digital advertising cost the industry $35 billion globally in 2020.
Other estimates put that number to be between $6.5 billion and $19 billion. Either way you look at it, ad fraud is a costly problem to all players in the digital advertising and marketing industries.
Over the years, many companies have emerged to offer ad-fraud detection and prevention software, such as CHEQ, DoubleVerify, WhiteOps, Pixalate, and Fraudlogic.
In addition, the IAB has introduced new standards to help combat certain types of fraud.
The IAB’s ads.txt standard aims to prevent domain spoofing and illegitimate inventory arbitrage by allowing publishers to state which companies are authorized to sell their inventory. Advertisers can then match that list provided by publishers with the platforms that are selling them ad space.
If there’s a match, then it means that the seller (e.g. SSP or ad exchange) is authorized to sell that particular publisher’s inventory. If there’s no match, then it could mean the seller is a fraudster or unauthorized to sell the publisher’s inventory.
Ads.txt is designed to work in the web browser environment, but domain spoofing and illegitimate inventory arbitrage are also found in in-app and over-the-top (OTT) environments, for which the IAB has developed app-ads.txt.
What Is app-ads.txt?
Released on March 13, 2019, app-ads.txt is an extension to the Authorized Digital Sellers (ads.txt) standard developed by the IAB Tech Lab. The main aim of app-ads.txt is to combat domain spoofing and reduce opaque practices like arbartary in in-app and over-the-top (OTT) environments.
How Does app-ads.txt work?
App-ads.txt works very much in the same way as its web-browser-based counterpart, ads.txt, but with a few slight differences. Mobile and OTT app developers create a list of the AdTech vendors that are authorized to sell or resell their ad inventory on their website in an app-ads.txt file. They then add a link to their website to their app store listings in the metadata.
<meta name="appstore:developer_url" content="https://www.app-dev1.com" />From there, media buyers (e.g. advertisers and media-buying platforms like DSPs) can crawl a database of app developer websites and translate the URLs into an app-ads.txt path to retrieve the app-ads.txt files. Then, DSPs can cross reference the app-ads.txt list with the information in RTB requests and see whether the given SSP or ad exchange is authorized to sell the app developer’s inventory.
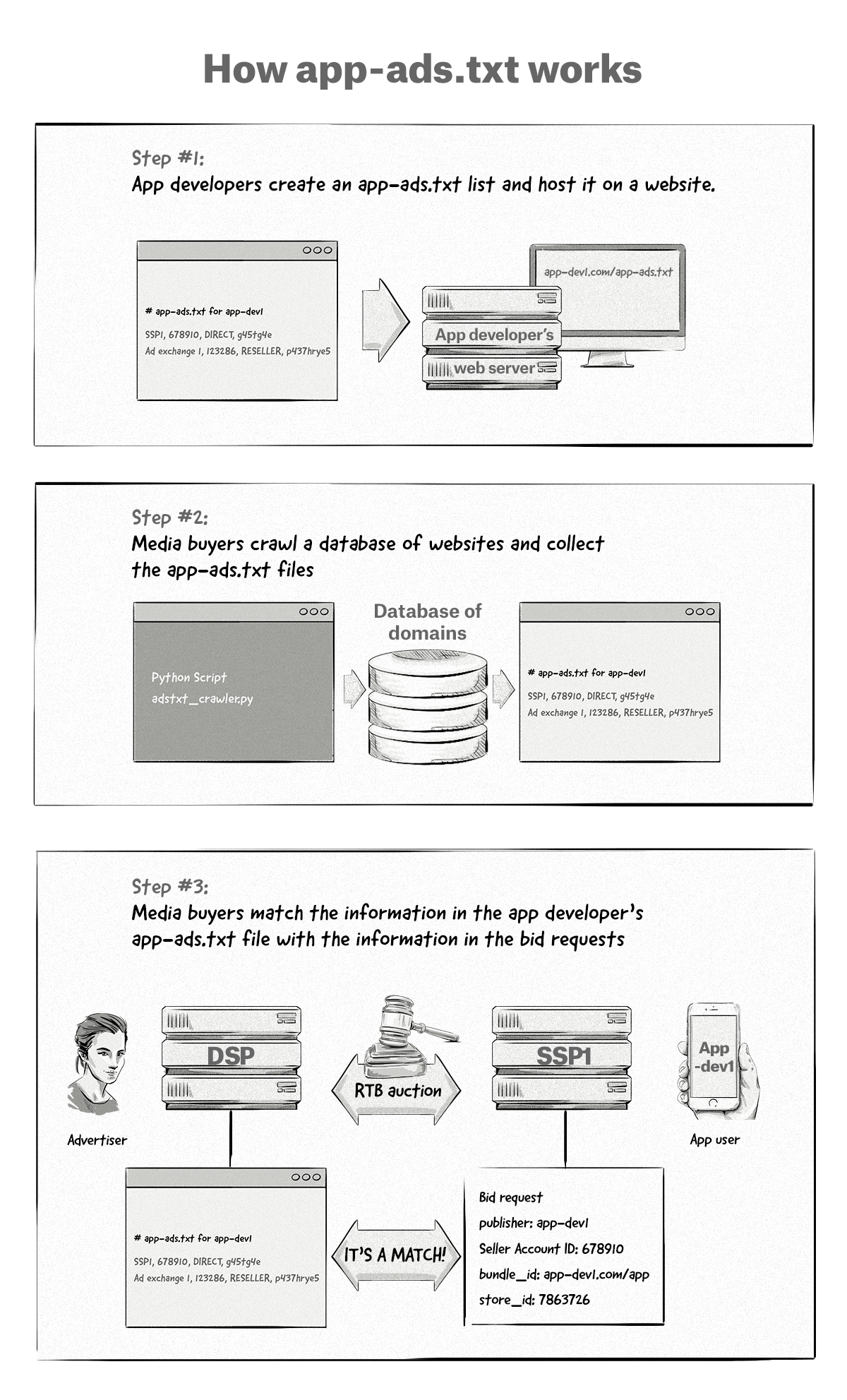
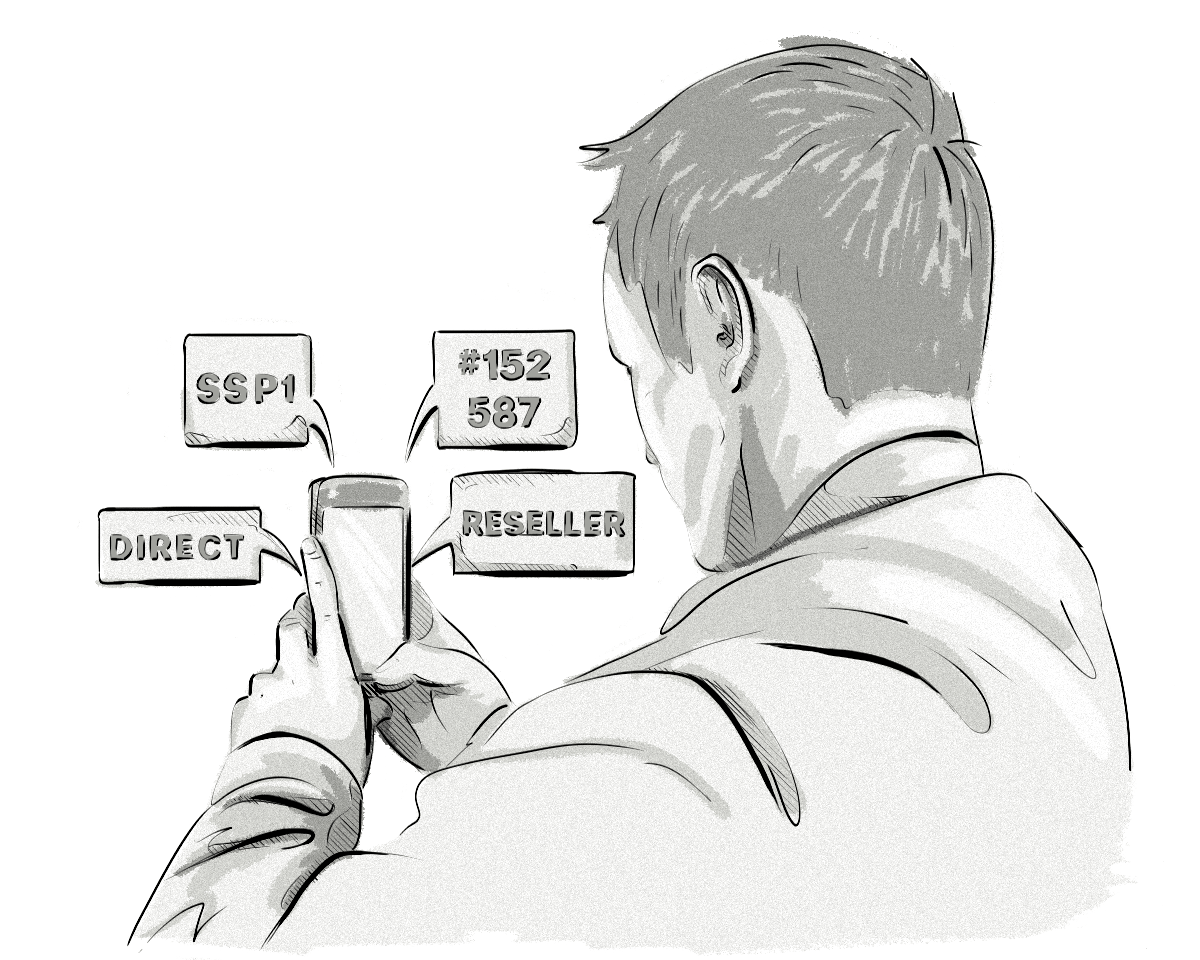
Here’s the information an app-ads.txt file contains:
SSP1 – The AdTech platform the publisher uses to sell their inventory. Examples include pubmatic.com, and magnite.com.
678910 – This field represents the Seller Account ID, which is also the publisher’s account ID for the respective AdTech vendors, and is used to verify the authenticity of the inventory during RTB auctions.
DIRECT / RESELLER – Direct means that the publisher works directly with the AdTech vendor to sell its inventory. Reseller means that the publisher has authorized another company (an ad network) to sell its inventory on its behalf.
g45tg4e – This optional field lists the Certification Authority ID, which identifies the advertising system within a certification authority, for example, the Trustworthy Accountability Group (TAG).
What Problems Does app-ads.txt Solve?
App-ads.txt aims to combat domain spoofing illegitimate arbitrage. Domain spoofing is an ad fraud technique that tricks DSPs into believing they are bidding on inventory from certain app developers (e.g. premium apps), when in fact they are just bidding on inventory from a low-quality or dummy app (i.e. an app created simply to carry out ad fraud).
Domain spoofing is frequently used to monetize sites and apps that would otherwise be blacklisted or ignored by advertisers and brands.
Arbitrage is a process where impressions are bought, repackaged, and then resold at a higher price by a third party.
Is apps-ads.txt Being Adopted?
Just like with most standards in programmatic advertising, the success of app-ads.txt lies in industry-wide adoption.
Pixalate, a fraud detection company that oversees ads.txt and app-ads.txt compliance, found that the use of app-ads.txt increased 177% between Q1 and Q2 of 2019. The number rocketed to 1,222% in the third quarter, reaching 111,875 implementations by the end of November 2019.
According to the IAB Tech Lab, more than 25,310 iOS apps and over 86,565 apps in Google Play have enforced the app-ads.txt file.
Mopub also states that the adoption rate among its managed app publishers is 82%.
And as reported by AdExchanger, many DSPs, including Centro, Google’s DV360, and The Trade Desk, are starting to enforce app-ads.txt, which will no doubt lead to higher adoption rates as ignoring this standard may lead to a loss of revenue.