Online advertising is a growing, multi-billion-dollar market. In 2020, it was predicted that global digital ad expenditure would reach US$225 billion — accounting for 44% of total ad expenditure. The sheer size of this market tempts criminals and hackers into creating technology and techniques to steal money from the advertisers.
The phenomenon of ad fraud existed from the beginning of online advertising, but in recent years it has been gaining traction as the real-time bidding (RTB) model is now being widely adopted.
The fragmented nature of RTB makes it easier to commit and conceal fraud.
In 2019, it was estimated that ad fraudsters would steal $5.8 billion from advertisers, however, because some types of ad fraud were very hard to detect and the technology to protect advertisers was immature, the actual figures were different.
But how are ad fraudsters able to steal this amount of money considering the sophistication of online advertising technology (AdTech)? Fake audience, fake users, fake traffic, fake clicks and fake installs – it all boils down to the same goal: advertisers are made to pay for exposure and clicks that never took place.
Below are 9 main types of online advertising fraud and how they work.
Ad Placement Fraud
This type fraud is performed by dishonest publishers who want to increase their revenues by generating more ad traffic.
Ad Fraud Technique #1: Invisible and Hidden Ads
This type of attack makes the ad invisible on the website, even though the impression will be reported. There are several techniques used in this type of attack:
- Display an ad in a 1×1 pixel iframe.
- Display the ads outside of the viewport area.
- Display (multiple) re-sized ads.
- Display several ads in an iframe loaded to a single ad slot, meaning that out of all the ads loaded, only one will actually be visible to the user.
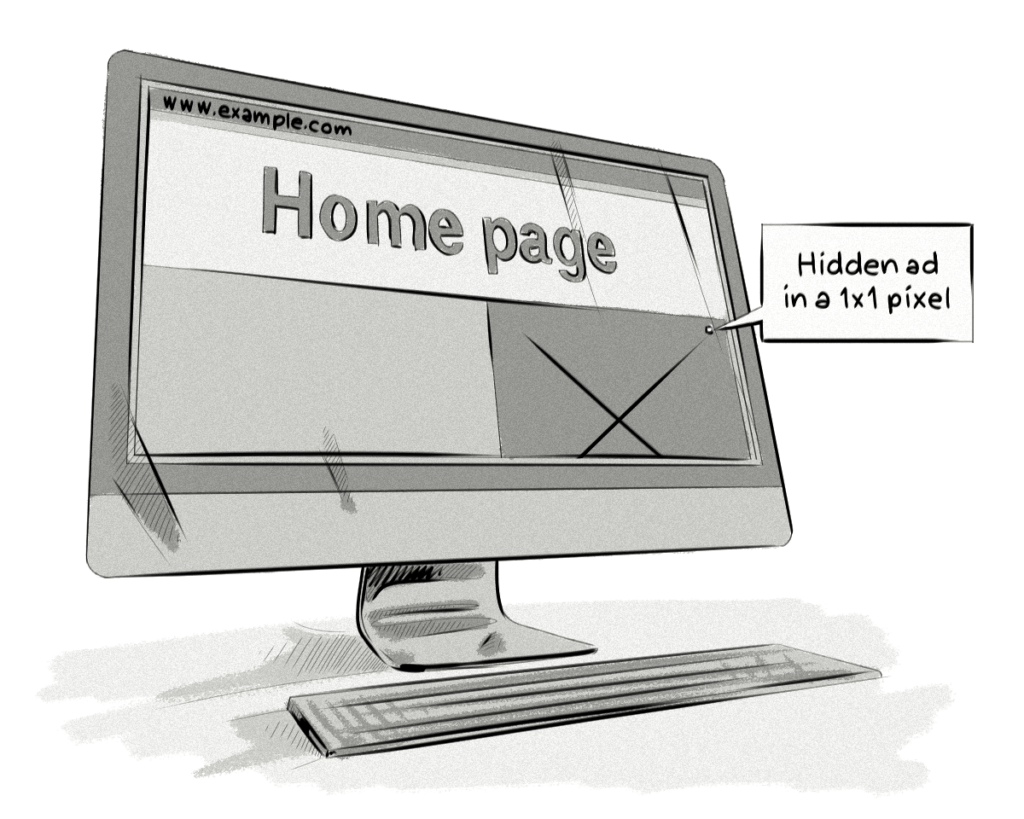
This type of fraud should not be mistaken with non-viewable impressions because banners that are properly displayed on the page but are not seen by the user (i.e. at the bottom of the page) are valid, accountable impressions.
You can find out more about the viewable impression model by reading my earlier article ‘Viewable impression tracking and pitfalls‘).
Ad Fraud Technique #2: Impression laundering
This type of attack conceals the real website where the ad is displayed.
Here’s how the process looks:
- The advertiser buys ads from a carefully selected publisher (one with a relevant audience and content that coincides with the advertiser’s brand), usually paying high cost per mille (CPM) rates.
- Part of the ad impressions bought by the advertiser are served on fraudulent websites where neither the audience nor the content is relevant to the advertiser’s brand (i.e. high traffic sites with illegal content which are traditionally hard to monetise).
- Through a number of complex redirects and nested ad calls through iframes, the ad calls are ‘laundered’ so that the advertiser sees legitimate sites instead of the actual, fraudulent sites where the ads are displayed.
Malware and Adware
Attackers perform these techniques by taking control over computers or browsers to generate ad revenues.
Ad Fraud Technique #3: Hijacking Ads
The so-called ad replacement attacks refer to the event in which the malware hijacks the ad slot on a website and displays an ad, generating revenue for the attacker rather than for the publisher (the owner of the website).
This could be done in a few ways:
- Compromise the user’s computer to change the DNS resolver (i.e. resolve the ad.doubleclick.com domain to the IP of the server controlled by the attacker, and therefore, serve different ads).
- Compromise the publisher’s website or the user’s computer to change the HTML content on the fly (change ad tags placed by the publisher to ad tags controlled by the attacker).
- Compromise the user’s proxy server or router (or the ISP’s router) to spoof the DNS server or change the HTML content of the site on the fly.
Ad Fraud Technique #4: Hijacking Clicks
Similar to hijacking ad placements, an attacker can hijack a user’s click.
When the user clicks on an ad, the attacker redirects the user to a different site, essentially stealing a prospective client from the advertiser.
There are a few ways in which the attackers can achieve this:
- Compromise the user’s computer to change the DNS resolver.
- Compromise the publisher’s website and hijack the click (i.e. by inserting an onClick event on the iframe with the ad).
- Compromise the user’s proxy server or router to spoof the DNS or change the HTTP request on the fly.
Ad Fraud Technique #5: Popunders
Popunders are similar to pop-up windows with ads with the exception that the ad window will appear behind the main web browser window, rather than in front. It can be combined with the impression laundering technique to generate additional revenue.
In some domains, it’s considered as a completely legal advertising method, but most of the ad networks forbid ads served in this way.
Ad Fraud Technique #6: Bots Traffic
Publishers can use botnet traffic, which either consists of compromised users’ computers or a set of cloud servers and proxies in order to:
- Achieve higher revenue targets
- Ensure eCPM growth
- Maintain comScore audience growth
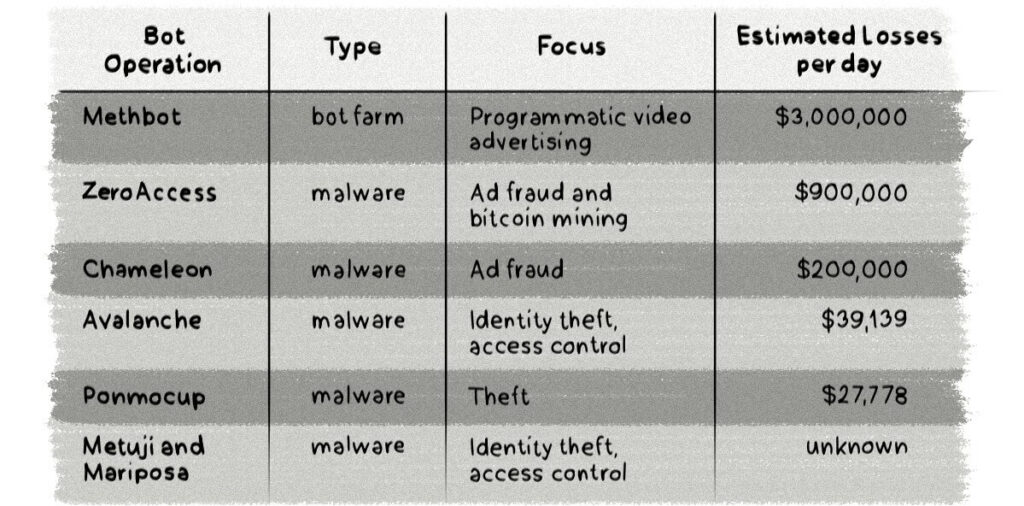
But there have been a number of large-scale botnet operations whose purpose was solely to generate revenue, with few actual business goals behind them. Methbot is the most profitable and most disruptive fraud operation discovered to date.
Methbot
Advertisers spending money on programmatic ad buying are losing more and more due to online advertising fraud.
Methbot, an elaborate fraud scheme detected in 2016, is considered one of the biggest and most profitable digital ad fraud operations to date. Discovered by White Ops, a US-based security firm, Methbot was found to be controlled by a Russian criminal group operating under the name Ad Fraud Komanda or AFK13. The fraud was estimated to pull in $3m to $5m from advertising every day, making the programmatic industry bleed cash.
Methbot was incredibly difficult to detect as the group used a number of efforts to disguise it as real human traffic. These methods included:
- Fake clicks and mouse movements
- Fake social network login information
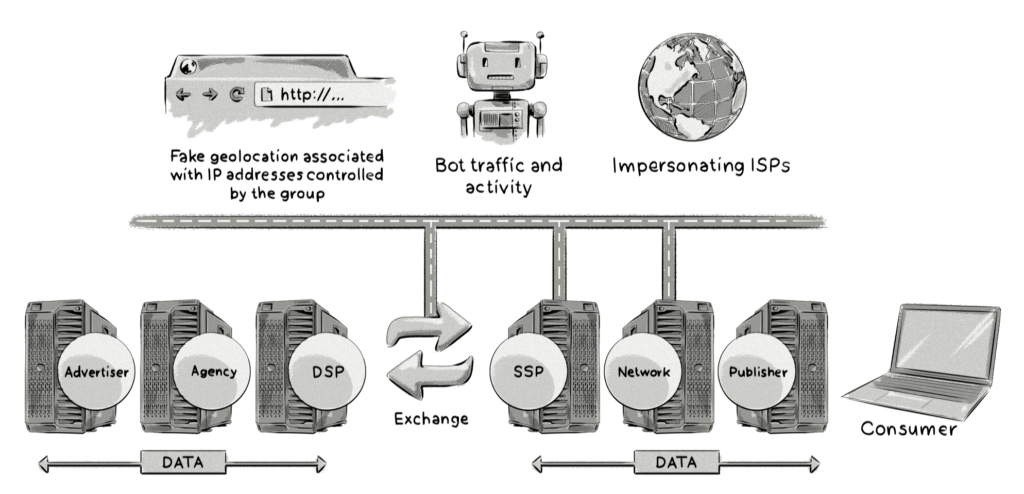
- Fake geolocation associated with the IP addresses controlled by the group
- Countermeasures against code from over a dozen different AdTech companies
- A custom HTTP library and browser engine with Flash support, all running under Node.js (a regular Internet browser can’t run hundreds of ads simultaneously)
- Dedicated proxy servers making it impossible to track the traffic to a specific source
The Methbot operation was very carefully planned and considered, and compromised several elements of the ad delivery chain. It not only impersonated premium sites and fabricated their inventory, but also disguised itself as legitimate ISPs. Then, methbot generated fake, human-like traffic which opened the ads on these fake premium sites. At the same time, with fake domain registrations, Methbot gamed the system by deciding where the most profitable ads should go, thus ensuring their fraudulent web space was purchased at maximum profit.
Mobile Apps and Ad Fraud
Mobile apps are becoming another increasingly lucrative target for fraudsters. This is mainly because ads in mobile apps are rarely blocked by ad-blocking software. Also, Android is generally considered more vulnerable to attacks due to its open-ended architecture which, coupled with the reach and size of the ecosystem, makes a very attractive and easy target for the fraudsters.
Ad Fraud Technique #7: Fake users
Just like in the case of desktop and laptop fraud, fraudsters also use mobile apps to imitate human-like activity. It typically involves a combination of methods like bots, malware and click or app install farms, all with the goal to build large audiences of fake users, and consequently feed on the online advertising ecosystem.
Click bots are designed to perform fake in-app actions. In this way, the advertisers are tricked to believe that a large number of real users clicked their ads while the ads never reach organic audiences.
Click farms use low-paid workers who physically click through the ads, earning CTR money for the the fraudsters.
Ad Fraud Technique #8: Fake Installs
Install farms are another way to imitate human-like behavior — they install apps using real people as dedicated emulators. Like in the case of fraudulent ad clicks, fraudsters use teams of real people who install and interact with apps en masse.
Increasingly often, fraudsters also use emulators to mimic real mobile devices. To remain untraceable, device farms regularly reset their DeviceID and avoid detection by using newly created IP addresses.
Ad Fraud Technique #9: Attribution manipulation
Bots are pieces of malicious code that run a program or perform an action. Bots aim to send clicks, installs and in-app events for installs that never actually happened. Fraudulent clicks, for example, are sent to an attribution system, gaming attribution models and falsely taking credit for user in-app engagement. While they can be based on real phones, most of them are server-based.
The objective of click fraud is to fabricate clicks on CPC-based adverts. There are two ways to do this:
Click injection – fraudulent apps downloaded by users generate fake clicks and take credit for the installation of other apps.
Click spamming (aka click flooding) – real, but hijacked (i.e. appropriated) IDs of mobile devices are used to send fake click reports. When a real user with that ID organically installs an app, the fake click will get the credit and make profit.
We Can Help You Build a Demand-Side Platform (DSP)
Our AdTech development teams can work with you to design, build, and maintain a custom-built demand-side platform (DSP) for any programmatic advertising channel.
How Is Ad Fraud Detected?
Because there are so many different types of ad fraud, detecting it is tricky. Luckily there are a number of companies out there that specialize in detecting ad fraud, with most offering a blacklist solution that prevents fraudulent activity from affecting future online advertising campaigns.
For the most part, these companies use algorithms to identify fraudulent behavior, such as abnormally high CTRs and poor or no campaign performance (e.g. 500 clicks but no conversions). From there, these ad-fraud detection companies can blacklist certain URLs and IP addresses.
Below is a list of the main ad-fraud detection companies:
- Fraudlogix
- HUMAN
- Forensiq, now part of Impact
- DoubleVerify
- Integral Ad Science
- Pixalate
The above ad-fraud detection vendors can be used by companies on both sides of the programmatic ecosystem, including demand-side platforms (DSPs), ad exchanges, ad networks, and supply-side platforms (SSPs) to detect and block this fraudulent activity during real-time bidding (RTB) media buys.
How To Fight Back Against Ad Fraud?
Despite the proliferation of fraud detection methods, fraudsters continue to invent new ways to exploit the system. Bots are becoming more and more sophisticated, making detection increasingly difficult.
Mobile app stores can resort to a number of methods to curtail mobile app fraud. Experts recommend developers regularly update SDKs, monitor their data for anomalies and perform regular fraud assessments. Certain outliers indicate a possibility of fraud (consider the chart below).
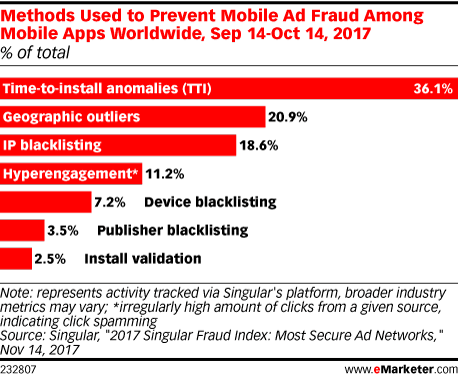
The study by eMarketer.com showed that time-to-install (TTI) anomalies helped to detect 36.1% instances of mobile ad fraud, followed by geographic outliers with 20.9%.
For an in-depth description of various examples fraudulent activity refer to a comprehensive post published by Kochava.
Ad Fraud: Examples and New Ways To Fight Them
New technologies emerge every year, as do new opportunities for fraudsters to take advantage of weak security processes and other technological vulnerabilities to make money fraudulently. At Clearcode, we track changes not only in “traditional markets” such as RTB, but also in “new” ones, such as programmatic audio advertising and CTV advertising.
Below you will find some examples of ad fraud schemes and news that highlights changes in how the market is fighting against them.
2020
- Oracle Exposes Largest CTV Ad Fraud Operation Ever
- How one botnet evolved its fraud to elude detection and steal revenue
- How Moat uncovered an in-game advertising fraud scheme
2021
- He called himself the King of Fraud. Now this bot lord will reign in prison for years
- DoubleVerify discovered an ad fraud scheme ParrotTerra
- HUMAN, Google, Roku, and Others Uncover a Sophisticated Ad Fraud Campaign Involving CTV Botnets
2022
- Smart Fridges Pose as CTV Devices in New Fraud Scheme
- App ‘Spoofing’ Could Cost Advertisers $135M (£111.7m) in 2022
- Studies find big increases in ad fraud attempts and fake traffic
- A new set of Best Practices for the Disclosure of Ad Fraud Attacks
- Pixalate Introduces Next Generation Patented IPv6-Enabled Ad Fraud Protection API Technology
- Edgemesh announces new feature to fight ad and click fraud
- DoubleVerify unmasked “ViperBot”, an ad fraud scheme spanning five million devices affecting CTV and mobile campaigns
2023
- HUMAN Discovers and Shuts Down Massive Ad Fraud Scheme
- DoubleVerify Takes Down First Large-Scale Ad Impression Fraud Scheme in Audio
Conclusion
It’s a constant arms race between online ad fraudsters and ad technology companies trying to prevent these types of fraud – similar to the war between hackers creating computer viruses and antivirus software companies.
Ad fraud is a serious problem permeating the advertising industry, and the losses it causes are skyrocketing. At the same time the mechanisms to detect fraud are mostly ineffective. But it doesn’t mean that advertisers should just throw in the towel. There are various technologies allowing advertisers to detect, prevent, and measure specific types of fraud:
- Ad delivery and visibility measurement
- Bluff ads (honey pots)
- Statistical models for detecting anomalies (see the chart above)
- Heuristic-based and machine-learning algorithms detecting fake traffic
- Website and botnet monitoring software
However, despite the advances in technology, ad fraud still appears to be a problem that will linger for many years to come due to continual growth of digital ad spend — after all, ad fraudsters follow the money.
We Can Help You Build a Demand-Side Platform (DSP)
Our AdTech development teams can work with you to design, build, and maintain a custom-built demand-side platform (DSP) for any programmatic advertising channel.